Build Trust Through Advanced Encryption Strategies Discover the Benefits of Encryption for Enhancing Digital Security Encryption […]
To fully comprehend the significance of SOC as a Service (<a href=”https://limitsofstrategy.com/soc-as-a-service-providers-in-india-2025-comparison-of-features-pricing/”>SOCaaS</a>), it is crucial to […]
This comprehensive guide is crafted for decision-makers seeking to thoroughly evaluate and choose a provider for […]
This detailed article serves as an essential resource for decision-makers focusing on the meticulous evaluation and […]
Expert Cybersecurity Guidance by Ezi Gold Marketing, Leaders in SEO & Digital Marketing Empowering readers across […]
Your Ultimate Resource for Finding Budget-Friendly Entry-Level Estates in Umhlanga Essential Features of Affordable Entry-Level Estates […]
Effective Strategies to Enhance Hosting Privacy Protections for Users Key Components for Establishing Strong Hosting Privacy […]
Ultimate Resource for Mastering DDoS Attacks and Their Business Implications In-Depth Analysis of DDoS Attack Mechanisms […]
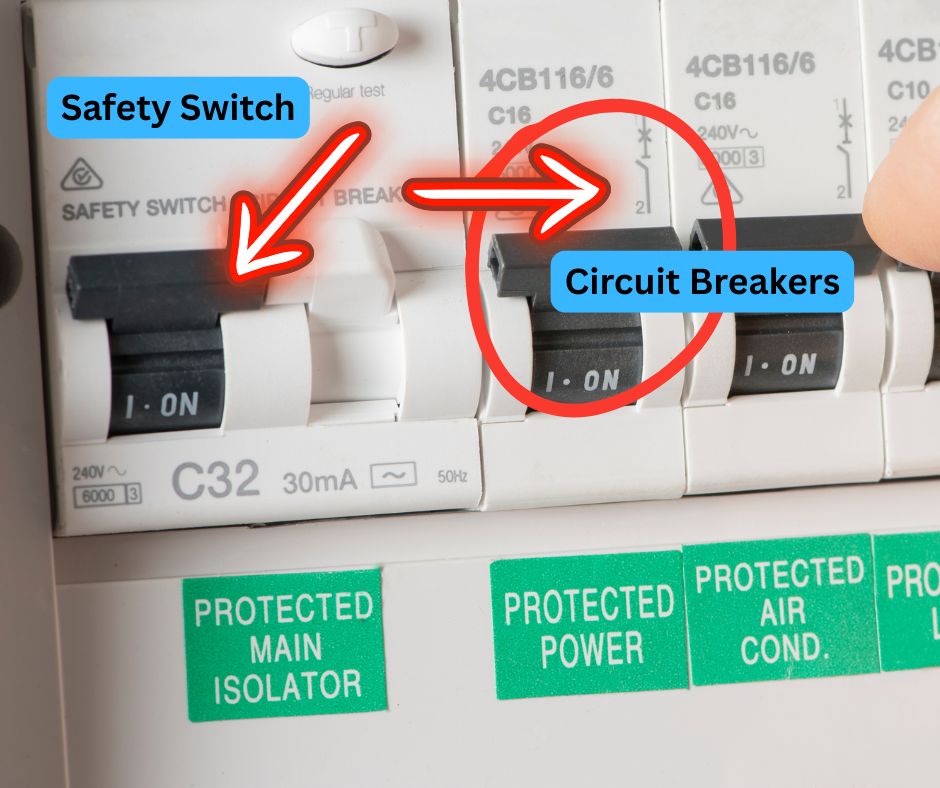
The Vital Role of Safety Switches in Protecting Home Electrical Systems In the absence of safety […]
Enhance Your Home Security with Professional Electrical Wiring Services The installation of your security system should […]









Recent Comments